Unintended Encryption, or, Much Cooler: Cryptoviral Extortion
The 'unintentional encryption' narrative creates a cartoonish framing around RANSOMWARE, as if you mistyped and hit control-z to undo the mistake. This overlooks critical questions about design choices, default security settings, and the fundamental art and science of computer security.

There's a euphemistic term "unintended encryption" that keeps appearing in my peripheral vision, and I keep turning my head slightly to notice the action, like a mouse running across the room or something. I remember first encountering it as part of a VMWare post, which I can no longer find, unfortunately, that used the amazing phrase "you have experienced an unintended encryption event". Sounds like something that might have happened in an AI-generated version of THE RUNNING MAN.
You Have Experienced an Unintended Encryption Event
This is a linguistic softening or biznification of RANSOMWARE, along the lines of downsizing, restructuring, streamlining, optimizing, re-engineering, de-layering, workforce rationalization, staff reduction, and organizational alignment, all those strange words and phrases and portmanteaus created to discuss layoffs and business failures.
I came across "unintended encryption" recently in an AWS post.
At Amazon Web Services (AWS), the security of our customers’ data is our top priority, and it always will be. Recently, the AWS Customer Incident Response Team (CIRT) and our automated security monitoring systems identified an increase in unusual encryption activity associated with Amazon Simple Storage Service (Amazon S3) buckets...It’s important to note that these actions do not take advantage of a vulnerability within an AWS service—but rather require valid credentials that an unauthorized user uses in an unintended way. Although these actions occur in the customer domain of the shared responsibility model, AWS recommends steps that customers can use to prevent or reduce the impact of such activity. - [1], emphasis added
Ultimately, yes, RANSOMWARE is certainly unintentional encryption, at least from the users perspective (not the attackers). No doubt there.
The shift in phrasing reveals the familiar business pattern of how security incidents are framed. The linguistic choice here shifts responsibility away from those who make the software, provide the services, etc., to the individuals, the ordinary people, who configure it.
RANSOMWARE
Ransomware is a type of malware that encrypts the victim's personal data until a ransom is paid. They commonly use difficult-to-trace digital currencies such as paysafecard or Bitcoin and other cryptocurrencies are used for the ransoms, making tracing and prosecuting the perpetrators difficult. Sometimes the original files can be retrieved without paying the ransom due to implementation mistakes, leaked cryptographic keys or a complete lack of encryption in the ransomware. [3]
I hate ransomware. I try not to use the word "hate" too much, but RANSOMWARE (RANSOMWARE!) is definitely something I hate.
Recently Toronto's public library went offline for MONTHS [4], yes MONTHS, due to RANSOMWARE.
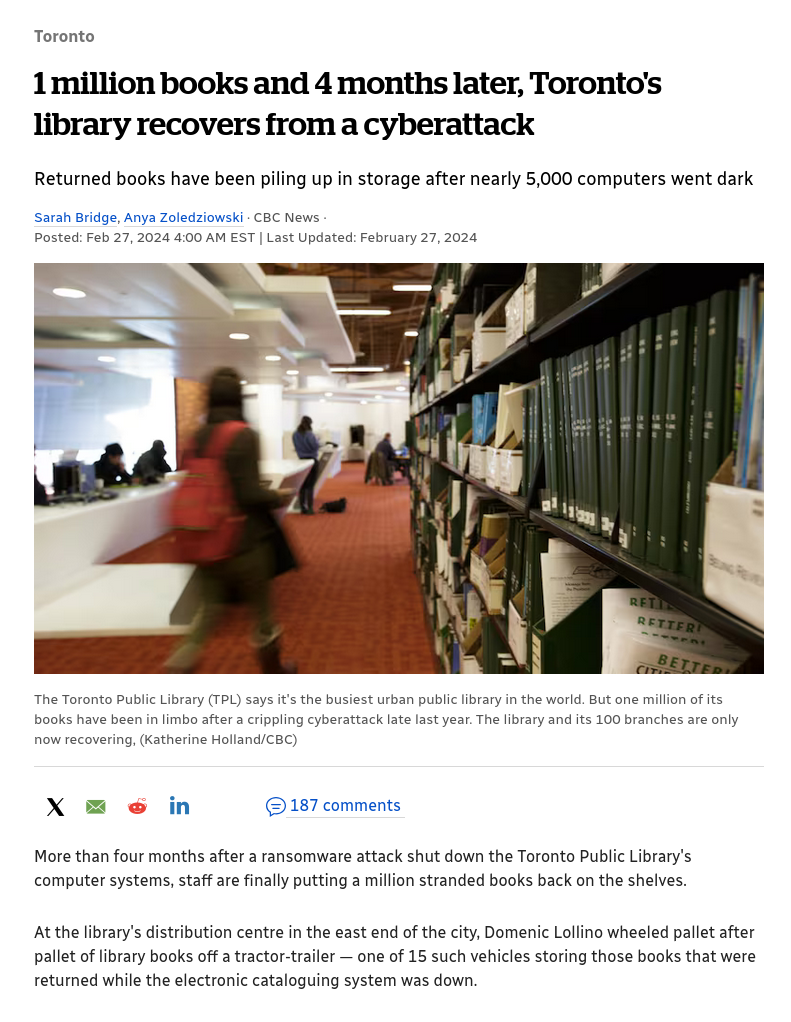
I mean, look at this image. "CAUTION DO NOT ENTER" tape wrapped around library computers. Really amazing.

Cryptoviral Extortion: Way Cooler

The paper in which Adam Young and Moti Yung invent the base concept for RANSOMWARE.
Traditionally, cryptography and its applications are defensive in nature, and provide privacy, authentication, and security to users. In this paper we present the idea of Cryptovirology which employs a twist on cryptography, showing that it can also be used offensively. [6]
Why say "unintended encryption" or "RANSOMWARE" when you could say "you have experienced cryptoviral extortion". If we're going to mess around with linguistics, let's make it harder not softer, e.g. "avoiding cryptoviral extortion."
Cartoonish
The "unintentional encryption" narrative creates a cartoonish framing around RANSOMWARE, that it is accidental in nature, as if you mistyped, encrypting a document, exclaimed "ooops," and hit control-z to try to undo the mistake–which is obviously not possible in the context of RANSOMWARE...the point is that the data has been encrypted with a secret or key that you do not know, and is therefore unrecoverable until the malicious actor provides it.
Framing RANSOMWARE as something that "just kinda sorta happens sometimes" due to human error causing misconfiguration overlooks critical questions about design choices, default security settings, and, just generally, the art and science of computer security.
Further Reading
[1] - https://aws.amazon.com/blogs/security/preventing-unintended-encryption-of-amazon-s3-objects/
[2] - https://redcanary.com/threat-detection-report/
[3] - https://en.wikipedia.org/wiki/Ransomware
[4] - https://www.cbc.ca/news/canada/toronto/toronto-library-ransomware-recovery-1.7126412
[5] - https://privacy-pc.com/articles/yes-we-cant-on-kleptography-and-cryptovirology.html
