Surivorship Bias & the Nation State Long Con. The Number of Software Backdoors Is Not Zero. We Are a Techno-Society That Depends on Open Source Software.
The open source software movement is one of the most interesting things to happen in recent human history. We are a techno-society that depends on open source software, so what happens when nation states go after the basic human frailty of OSS maintainers?
The open source software movement is one of the most interesting things to happen in recent human history, especially given the tremendous commercial value, the relative strangeness of the act of writing code itself, and how we maintain that code over long, long periods of time.
Technically, code is copyrighted as soon as it is written, just like anything we write. But some people have chosen to license that code with open source software (OSS) licences, making it free for others to use. Thus, as we know, code becomes like a library where we can borrow other people's work and incorporate it into our own. It's really quite an amazing and strange phenomenon, strange because 1) it's like writing, and 2) it has tremendous commercial value, 2) unlike a book, which usually never changes, code has to change, and the authors of these borrowed texts are asked to update them again and again, forever.
I would argue that it is not possible to write commercial software of any kind without using some form of open source software. To do anything in software, we need a massive amount of code (compilers for instance). It takes millions and millions of lines of borrowed code to deploy and run even a simple "hello world" application. And while many people are happy to do this kind of work, to support all these "hello worlds", for many it is a heavy burden, with all sorts of psychological effects. Software is people.
We have a lot of people working, often alone, on evenings and weekends, spending time away from friends and family, to support an important piece of code that is used in another extremely important piece of code, which is used in another system to secure it, which is used by everything to run its code, and so on. It's a social experiment that has enormous implications for how our (now) techno-societies work.

As we can see from the XKCD cartoon, this has long been a recognized problem. Creating something in demand for free can become a considerable burden, and anyone can stop or start contributing to open source software relatively easily. This is simply the way it works in what are effectively continuously changing and flowing volunteer situations.
What's more, due to these facts, we've postulated that a nation state could take advantage of this and put backdoors into software. With what happened last week with xz/liblzma, we can now be absolutely, 100% sure that this is happening and will continue to happen, and that there is no real easy solution to this, because dealing with it means dealing with human factors, which the technology industry is not good at, and never has been.
xz/liblzma
I don't want to spend too much time going over the recent incident as others have done that very well, and the analysis is still ongoing.
I'll try to lay out the major points in short form:
- There is a widely used open source library called liblzma.
- This library has been backdoored by a contributor who is presumed to be a nation state actor, and the way they went about doing is what I would consider a "long con."
- 'A "long con" or "big con" (also, chiefly British English: long game)[3] is a scam that unfolds over several days or weeks; it may involve a team of swindlers, and even props, sets, extras, costumes, and scripted lines. It aims to rob the victim of a huge amount of money or other valuables, often by getting them to empty out banking accounts and borrow from family members.' - https://en.wikipedia.org/wiki/Scam
- The backdoor is not in the code itself, instead malicious code is added during the build process.
- "Second-stage artifacts within the Git repo get turned into malicious code through the M4 macro in the repo during the build process. The resulting poisoned xz library is unwittingly used by software, such as the operating system's systemd, after the library has been distributed and installed. The malware appears to have been engineered to alter the operation of OpenSSH server daemons that employ the library via systemd." - https://www.theregister.com/2024/03/29/malicious_backdoor_xz/
- The backdoor was somehow, amazingly, discovered by an open source contributor working at Microsoft.
- "After observing a few odd symptoms around liblzma (part of the xz package) o n Debian sid installations over the last weeks (logins with ssh taking a lot of CPU, valgrind errors) I figured out the answer: The upstream xz repository and the xz tarballs have been backdoored."
- The way the contributor was able to gain access to get commit rights is likely a nation-state long con, and in this particular case it was based on the fact that the maintainer was a human being who, for various reasons, some of which may have been manipulated by the attacker, decided to pass the mantle of maintainer to the malicious actor.
- The presumed nation state actor also made contributions to other open source libraries and systems to hide their backdoor.
Survivorship Bias
Survivorship bias is a form of selection bias that can lead to overly optimistic beliefs because multiple failures are overlooked, such as when companies that no longer exist are excluded from analyses of financial performance. It can also lead to the false belief that the successes in a group have some special property, rather than just coincidence as in correlation "proves" causality. - https://en.wikipedia.org/wiki/Survivorship_bias
There have been some takes on this particular event/issue that suggest that because of the openness of OSS (and the efforts of a single individual), we as an ecosystem were able to stop the backdoor from eventually infiltrating a large percentage of SSH servers running around the world, and that this ability extends to all threats to OSS.
I don't deny that the idea of openness, the concept of "many eyes" that comes with OSS, is a good thing. But this xz attack was extremely sophisticated, and I don't believe for a second that this is the only one of these attacks that exists; that this is the only one that's in play. Instead, I believe that we just happened to be diligent enough in this particular case; that we will not and cannot catch all attacks.
We have survived this particular event. But this is an example of us assuming that the "planes that have returned" are what we need to fix, and that we should be reinforcing the areas that show damage, as opposed to reinforcing the areas that don't show damage, which were the planes that didn't return.
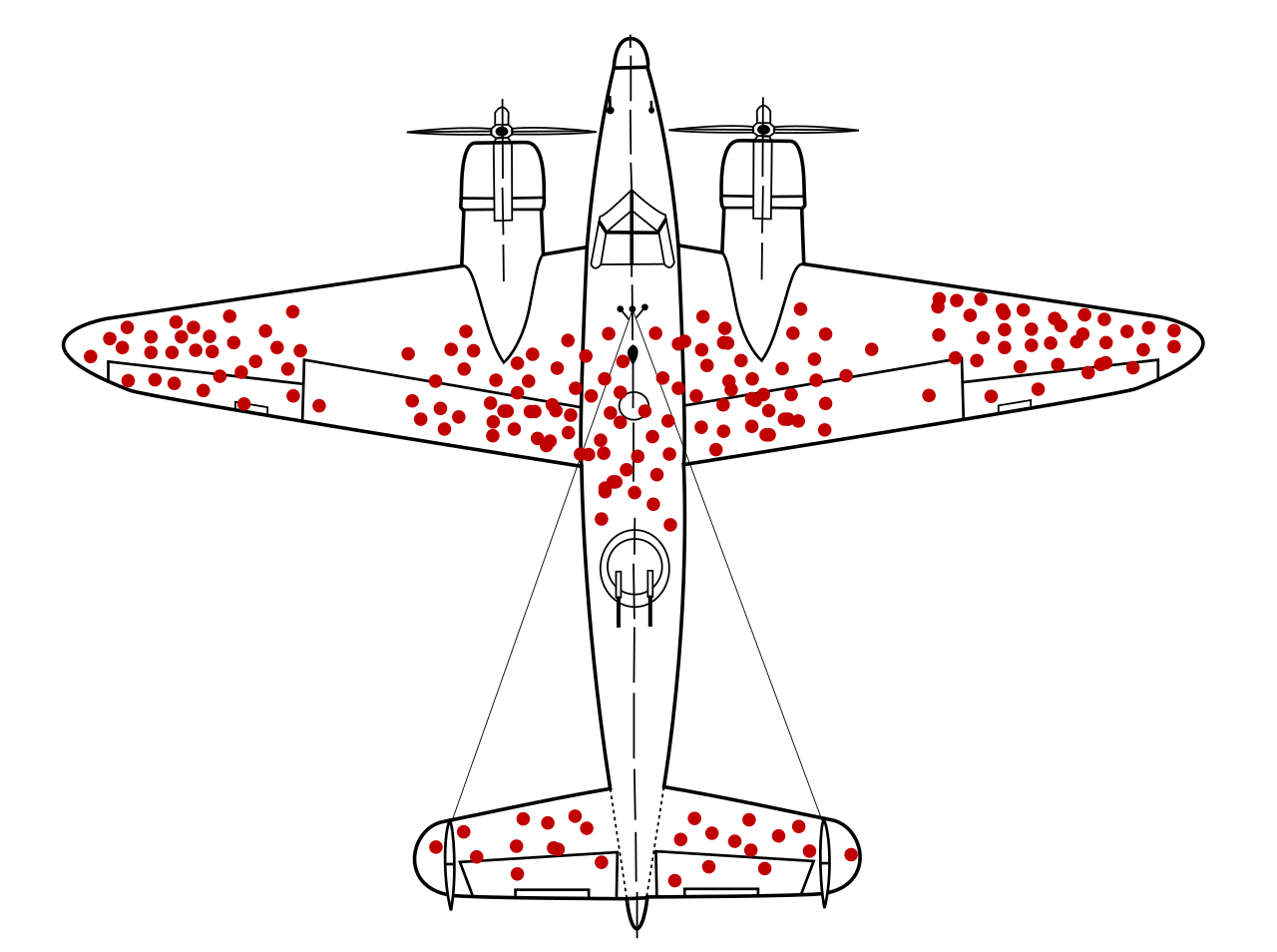
This hypothetical pattern of damage of surviving aircraft shows locations where they can sustain damage and still return home. If the aircraft was reinforced in the indicated areas, this would be a result of survivorship bias because crucial data from fatally damaged planes was being ignored; those hit in other places did not survive. - https://en.wikipedia.org/wiki/Survivorship_bias
There are many opinions on this, but my belief is that there are non-zero backdoors now, at this time, and that there will be more attempts that both fail and succeed in the future.
Human Frailty
What's more, the way that this attack was accomplished is not the only way that they will be performed.
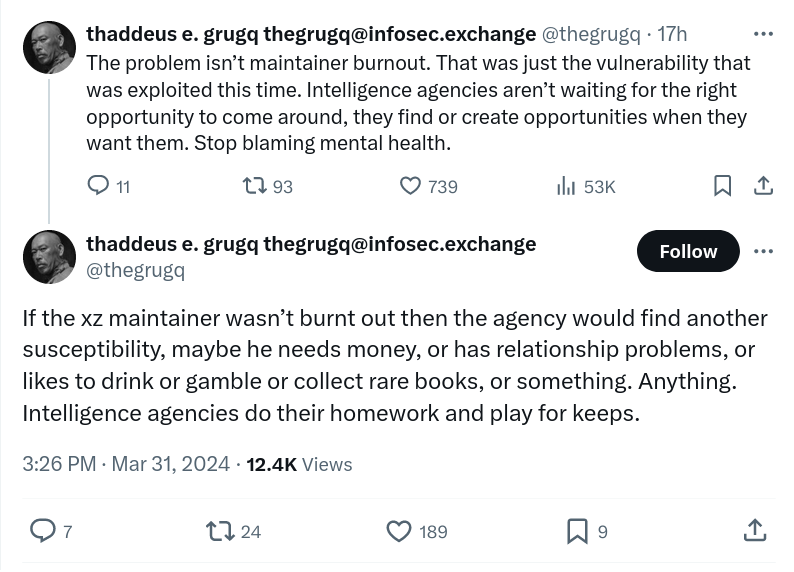
These are attacks not on technology, but human beings, and all our inherent frailty.
Are We Willing to Admit We Are a Techno-Society?
We are good at writing software–a lot of software–which is a difficult and highly technical thing to do. However, we are not as good, strangely, at the human side of writing software, especially in the open source world, where the motivations are personal and voluntary and the remuneration is not related to the true commercial (and societal) value of the software. How can we make the lives, the work, of open source maintainers better, and help them to understand that nation states will attack them, so that the software they create is more secure? This is an extremely difficult problem, and one that has more to do with the human side of national security than with the technological side. We can't apply technology to this problem, we have to apply our social skills to it.
We are now a techno-society, and we have to find ways to protect that technology, but to do so with the people who create it in mind.
Additional Related Links




https://t.co/PrIjMtt81r pic.twitter.com/lMy68hCpxO
— Michael Gattozzi (@mgattozzi) March 30, 2024



