The Cybersecurity Attack Surface Is Getting Bigger and Bigger. We’ve Been Going Through a Mega-Evolution. It’s a Hypersurface Now.
We've invented and evolved thousands of computational thingamawhatsits to deploy applications with, and combined them in billions of permutations...then we need to build the cybersecurity around them. It's worth it to take a moment, step back, and ponder that.

We used to name computers after, oh, I don't know... Lord of the Rings characters. Anything really, chocolate bars, baseball teams. Some companies still name servers or services, for example Cloudflare has hundreds of servers with names like bob.ns.cloudflare.co and lola.ns.cloudflare.com
Another example from one of the funniest IT-related shorts of all time, "Microservices" where we have services like "Galactus" and "OMEGA STAR," and, er, "Basketball."
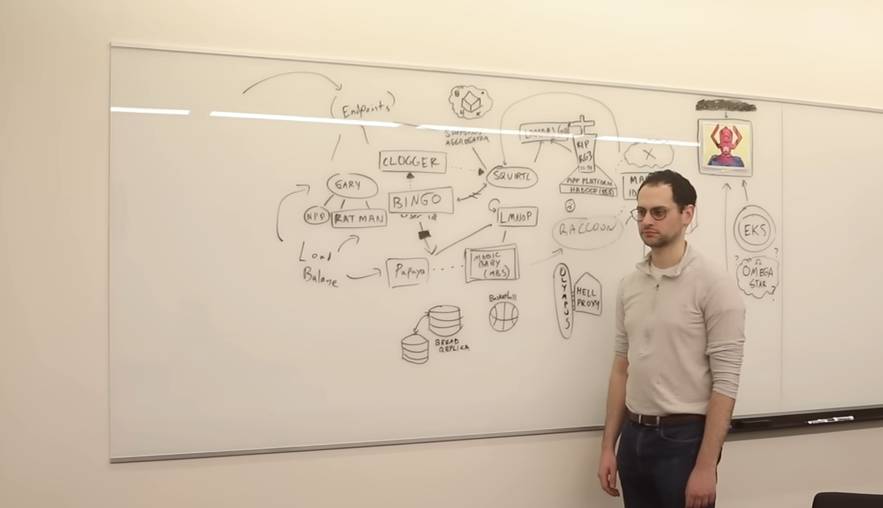
When your microservices constellation looks like the below, there's simply too many to remember names.

But I digress. My point here is that times have changed. We no longer give our servers names, instead they are represented, in the public cloud, by what is effectively a random number.
Here is your server now: a string of digits. Same with almost any object in the public cloud. The names don't matter any more.
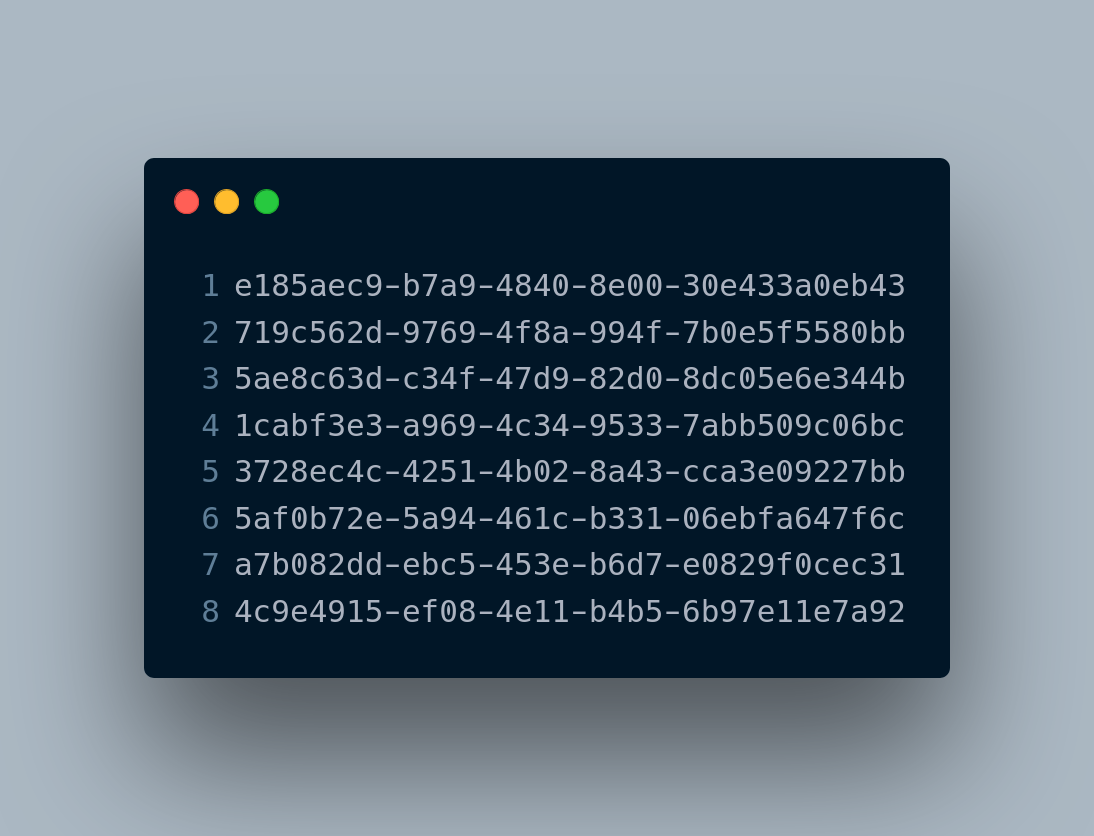
Mega-Evolution
On the one hand, the evolution of the public cloud and technology in general is obvious. "The Cloud" is a cultural phrase. But on the other hand, it's a bit like the idea of a frog slowly boiling in water...we don't necessarily notice, or perhaps we don't take the time to step back and look at, just how much things have changed. And things have changed indeed. We've been getting new things, new technology, continuously, for years, and the amount and speed is ramping up.
Instead of having one big server, let's say when we first started building electronic computers, we now have thousands of virtual machines, containers, identities, roles, permissions, available services, abstractions like Kubernetes (which has its own identities), and non-human aka machine identities, to name a few. And these things come together in complex, unique permutations that can only be understood, if at all, in a programmatic fashion.
It's been a mega-evolution.
From about 570 to 530 million years ago, an evolutionary burst of life forms occurred, often referred to as the “Cambrian Explosion.” This marks an important point in the history of life on earth, as most of the major lineages of animals got their starts during the Cambrian Period and have been evolving ever since. - https://evolution.berkeley.edu/the-arthropod-story/meet-the-cambrian-critters/the-cambrian-explosion/
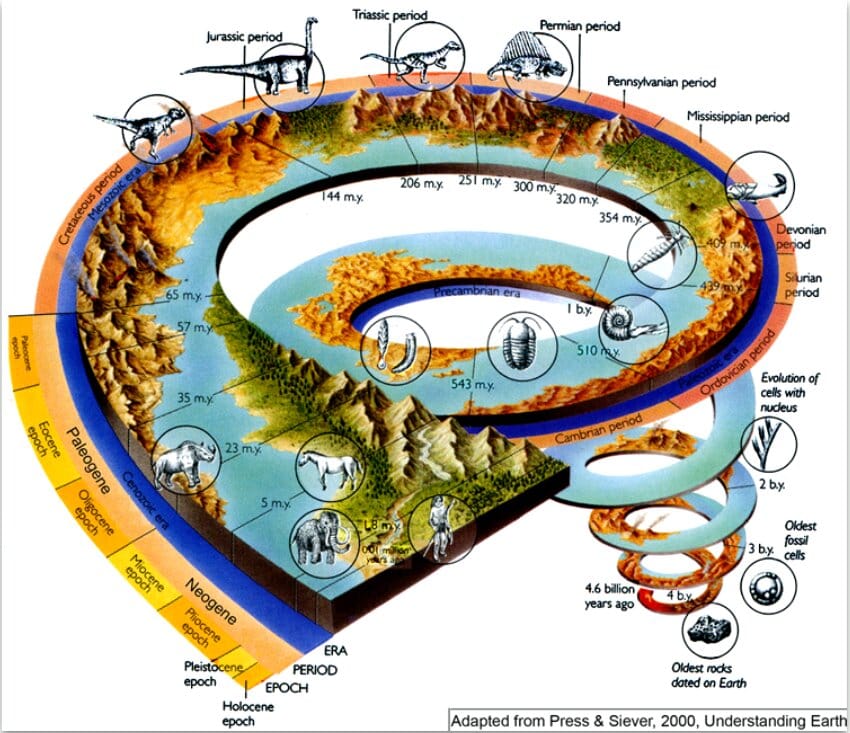
In many ways we've gone from one or two "dimensions" to a multidimensional array of complexity. To mix metaphors, we've gone from a few simple animals to rapidly evolving organisms with thousands and thousands of combinations.
We Have To Invent New Things To Deal with the New Things We’re Inventing
Did the firewall get invented at the same time as TCP/IP? No, we had to wait quite a while before getting "firewall technology," for better or worse.
TCP/IP:
The work on TCP and IP dates back to the 1970s. Vinton Cerf and Robert Kahn submitted the first-ever paper on the internet, titled “A Protocol for Packet Network Intercommunication.” at the IEEE Transactions on Communications conference in 1974. - https://www.geeksforgeeks.org/history-of-tcp-ip/
Firewalls:
In 1988, Digital Equipment Corporation (DEC) developed the first generation of firewall technology called the Packet-Filter Firewall. - https://www.thepcinsider.com/who-invented-firewall-history-evolution-types-generations/
and:
The first paper published on firewall technology was in 1987 when engineers from Digital Equipment Corporation (DEC) developed filter systems known as packet filter firewalls. - https://en.wikipedia.org/wiki/Firewall_(computing)
So it is the same with public cloud and modern computing, where we have more than a few dimensions of complexity to deal with, and so we are inventing new technologies to help us in these areas, and the work is ongoing.
It's not enough to just adopt the Lego bricks of the public cloud, we need new technologies to help us manage the huge attack surface that we're adopting, to understand what exactly it is that we are building with these extremely complex computing puzzle pieces. This is part of why cybersecurity is so challenging. We're creating new hi-tech creatures like it's a video game.
We have to manage:
- Vulnerabilities in code and other artifacts
- Identities and entitlements
- Machine identities and entitlements
- Configuration posture
- Cloud detection and response
- Software as a service (SaaS) platforms
- Constant updates of recommended roles, configuration options, etc
- +++++
And we will invent new technologies, and then new technologies to help us with the cybersecurity of those technologies. My point is that we're still in the early days of computing in general, it's only been about 90 years of electronic computing, and we're still in the first inning of our computing explosion, and it's important to step back from time to time and realise where we are and how we got here, and to try to understand how the mega-evolution of technologies has changed the way we approach cybersecurity.
PS. Book Recommendation
Sometimes things get so big (and weird) that they're hard to understand; your mind can't wrap itself around the whole concept, and they become "hyperobjects". The public cloud is clearly a hyperobject, and the hyper (attack) surface is part of that hyperobject.
Global warming is perhaps the most dramatic example of what Timothy Morton calls “hyperobjects”—entities of such vast temporal and spatial dimensions that they defeat traditional ideas about what a thing is in the first place. Morton explains what hyperobjects are and their impact on how we think, how we coexist, and how we experience our politics, ethics, and art. - https://www.upress.umn.edu/book-division/books/hyperobjects

