Cyber Deterrence
We've long been under the global spectre of MAD, mutually assured destruction, but that's only one model of deterrence. We also need to examine what deterrence means in the context of cybersecurity.

In this post I discuss some aspects of Ben Buchanan's 2014 paper Cyber Deterrence Isn't MAD; It's Mosaic, where M.A.D in this case stands for "mutually assured destruction," which we usually associate with...well...with TOTAL. NUCLEAR. WAR.
[Deterrence is] the art of making another actor decide not to do something because of the threat of reprisal.
Deterrence is usually associated with the idea of everyone collecting as many big sticks with as many sharp nails in them as possible, the point being to ensure that we all have at least one nasty-looking weapon, and that if someone else uses their weapon on us, we use ours to reach out and touch them painfully in return. Ultimately, we build out the the possibility of an eye-for-an-eye model of reprisal, which will, in theory, deter any particular actor from doing something malicious to another actor.

However, we should not think of deterrence as only absolute and strategic.
...the fading memory of the Cold War should not leave a monolithic concept of deterrence as its legacy. In facing new threats and new actors, governments must develop a more nuanced and multi-faceted understanding of deterrence. Perhaps in no case is this more apt than threats in cyberspace. This article contends that there is no single way to deter an adversary's cyber operations.
This all said, a key point about this paper is that it is mostly referencing state-level actions. Non-state actors are not capable of "attacking back," unless we're talking within the context of a high-cyberspace William Gibson novel (see ICE, Intrusion Countermeasures Electronics). The point of the paper is not to discuss how non-state organizations can implement deterrence. Ultimately, unless you are a governmental agency, there is no deterrence option. And yet there are interesting facets of this field which apply to non-state organizations and businesses.
The Uniqueness of Cybersecurity
Cybersecurity is fascinating, for many reasons, a few of which I list below.
- It's asymmetric - Adversaries may have less power, but can use that power in unconventional ways.
- It's adversarial - Adversaries are tricky human beings.
- It's optional - We don't need cybersecurity to build problem-solving software.
Additionally, from Buchanan's paper, we find that there is "no single way to deter an adversary's cyber operations." Thus I could add the lack of deterrence to my points on cybersecurity.
- It's asymmetric
- It's adversarial
- It's optional
- There is no deterrence - For non-state actors, that is.
Mosaic
A significant portion of the paper concerns the idea of the "mosaic" model for approaching deterrence. The notion of total nuclear war and MAD is rooted in our society. We have lived under the spectre of nuclear armageddon for quite some time, and while the Cold War™ has faded away, a newer, more alien and difficult to understand version has taken its place, especially now that Russia has invaded Ukraine. It's not exactly the Cold War, but it's not exactly not-not the Cold War either.
Vladimir Putin has ramped up his nuclear rhetoric, saying his country had successfully tested the nuclear-powered, nuclear-capable Burevestnik strategic cruise missile, as he suggested Russia could resume nuclear testing for the first time in more than three decades. - The Guardian, Oct 5th, 2023
However,, while in many ways we are still stuck with some form of nuclear MAD, it is only one kind of deterrence.
In this two dimensional model [shown below], The United State's Cold War deterrence strategy that is so familiar to modern international relations theory is in fact just one type of deterrence against one type of threat: absolute deterrence against the specific Soviet nuclear threat.
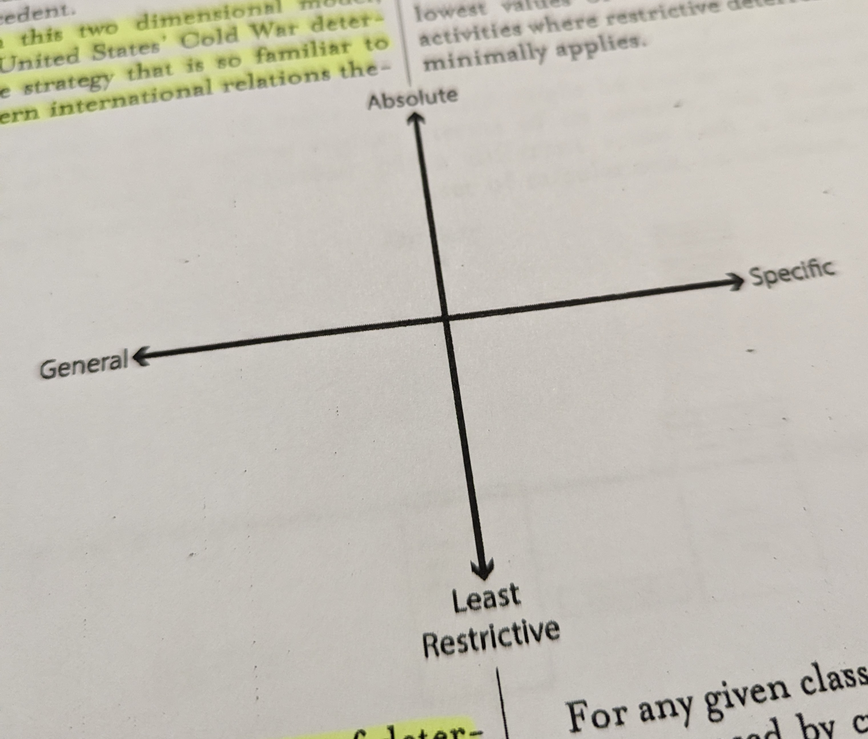
Here, Buchanan puts forward the concept of a mosaic.
...there is no single dominant strategy that meets each cyber challenge...the United States should construct a mosaic of different deterrence strategies to confront the full spectrum of cyber threats. The differences in these assorted types of deterrence loosely correspond to the found quadrants of the model [above].
But...Non-State Organizations Can Have as Much Defence They Want!
An interesting thought in this paper is around how, with regards to traditional warfare and international conflict, excessive defensive capabilities can actually be destabilizing, but that is not true for cyber defense.
Historically, in situations that call primarily for absolute and specific deterrence--such as the Cold War--excessive defensive measures can be destabilizing because they hamper an adversaries ability to perform a second strike...in the case of cyber deterrence, as in criminology, defense is not destabilising.
This is an interesting observation in that non-state actors can implement as much cybersecurity defence as they like. So, this may be an advantage. However, of course, as an industry we find it incredibly onerous, expensive and inconvenient to implement cybersecurity, so it is difficult to take advantage of this additional defensive latitude we have been afforded.
Again, we could add to that list.
- It's asymmetric
- It's adversarial
- It's optional
- There is no deterrence - For non-state actors, that is.
- The amount of allowable defense is unlimited - For non-state actors, that is.
